04. System Event Logs
System Event Logs Heading
System Event Logs
ND545 C02 L03 A07 System Event Logs Part 1
System Event Logs Notes
Recap:
- Event logs are records of events that take place on the computer.
- Used for troubleshooting and auditing.
- Perfect for setting alerts on suspicious events.
- 3 Primary Categories of Event Logs in Windows
- System The System event log is for general system events, Services starting and stopping etc.
- Security The Security event log is for login attempts and permissions events.
- Application The Application log is for events associated specifically with applications. Think Office or Adobe.
- There are 5 Types of Events.
- Error An error represents a real problem with the system. A hung Service or a Disk that is failing.
- Warning A Warning is an event that indicates a pending problem, low disk space for example.
- Information This is the most common event, it simply logs that an event took place successfully.
- Success Audit A Success Audit is when an audited event was successful. Such as you typed your password in correctly to login.
- Failure Audit A Failure Audit is when an audited event was unsuccessful. When you attempt to access a folder without permissions for example.
System Event Logs Image
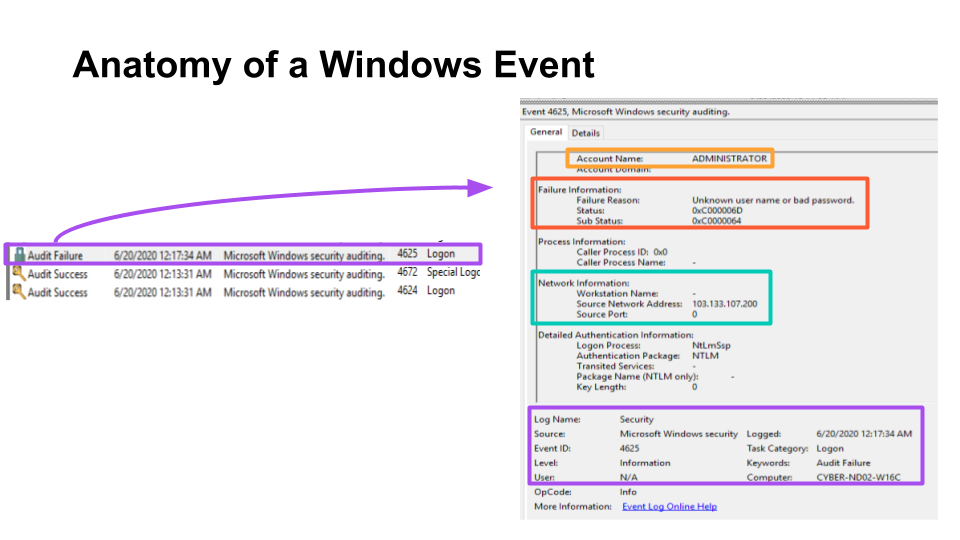
Anatomy of a Windows Event
Additional Thoughts:
- There are actually 2 additional event logs in standard Windows installations. They aren't used quite as much.
- Setup The Windows Setup Event log contains events that occurred when the operating system was being installed.
- Forwarded Events If the particular machine you are on has forwarded events that indicate that another Windows install on your network is sending its logs to your machine. We'll cover this topic more later.
Additional Resources:
System Event Logs Further Research
Linux Logs
ND545 C02 L03 A07 System Event Logs Part 2
Recap:
- CentOS logs are stored in /var/log
- We installed the application Audit to make viewing logs easier. There are other applications as well.
- Here are some logs that you may consider alerting on:
- Failed Login Attempts
- Cron jobs, these are scheduled tasks and can be used to establish persistence
- Yum updates, in particular if the machine should not be receiving updates
- There's likely to be logs for the applications your Linux server is hosting that are worthy of alerts.
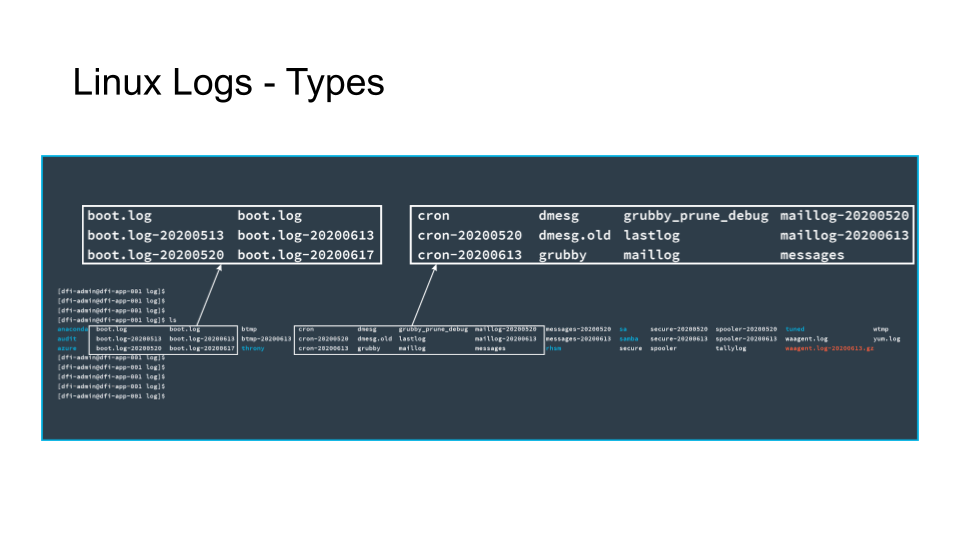
The text in white represents files.
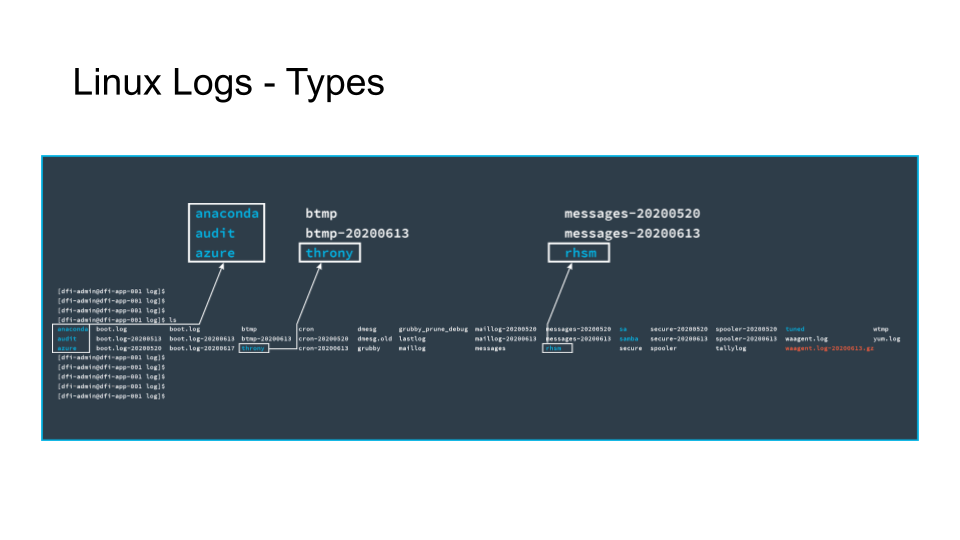
The text in blue represents directories.
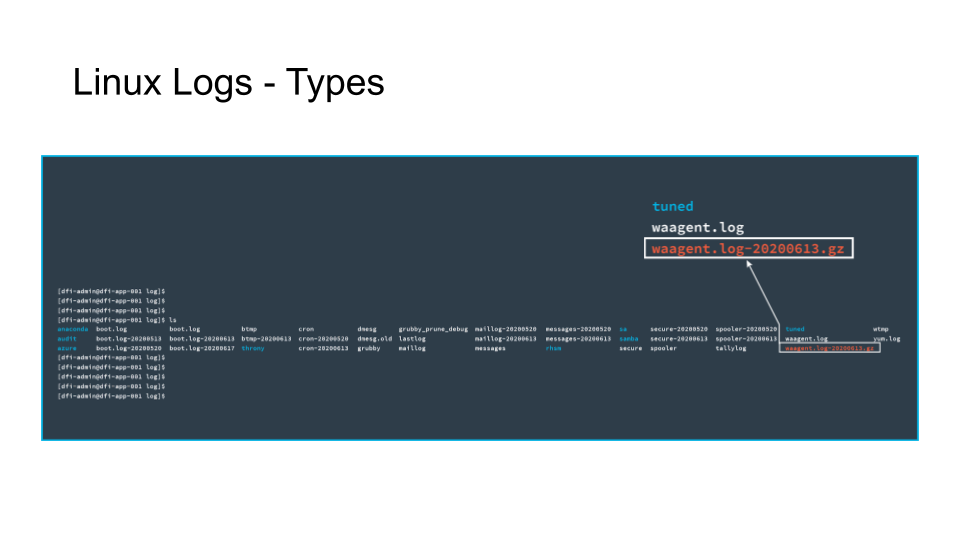
The text in red represents an archive file.
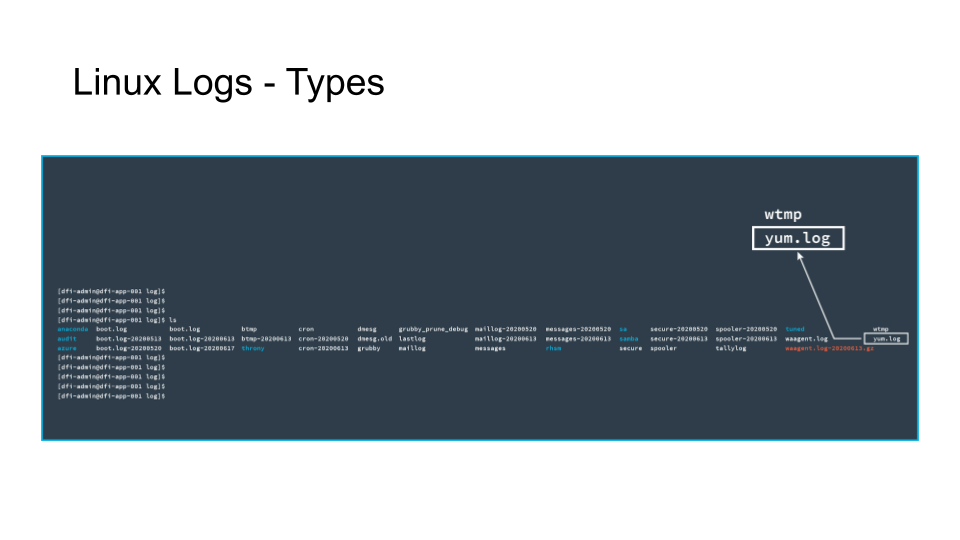
An example of a log file you may be interested in, the Yum log.
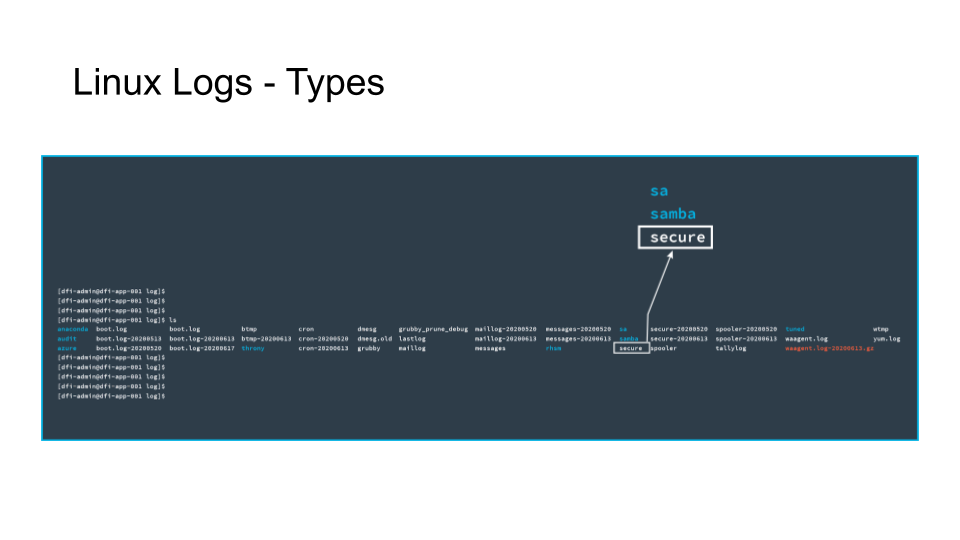
The Secure log file is where successful and failed login attempts reside.
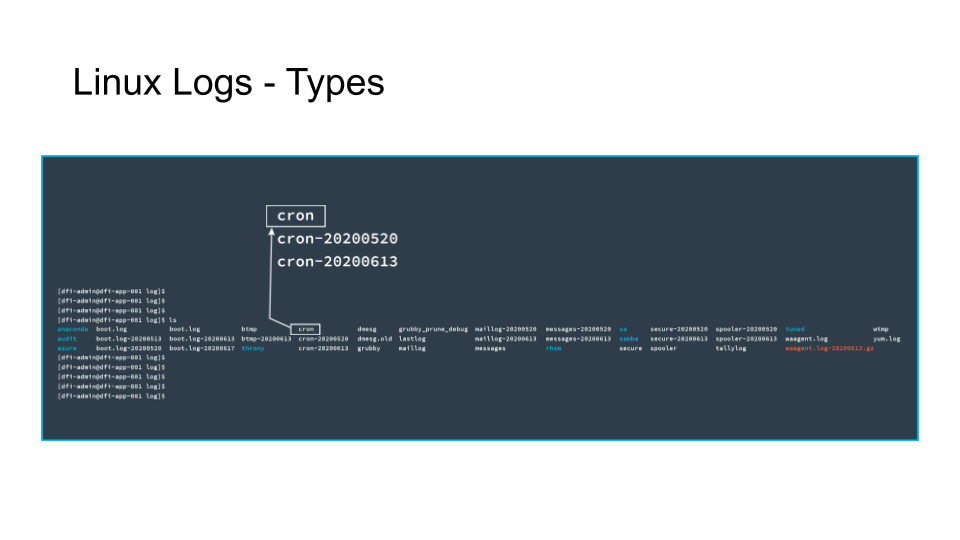
Cron log contains information on scheduled tasks.
Windows Walkthrough
ND545 C02 L03 A08 System Event Logs Walkthrough Part 1 Windows
INSTRUCTOR NOTE:
Command: Get-EventLog -Logname Security -InstanceID 4625 -Newest 25
Linux Walkthrough
ND545 C02 L03 A08 System Event Logs Walkthrough Part 2 Linux
INSTRUCTOR NOTE:
Command: sudo aureport -au -i --failed | more